Many Small to Midsize businesses are having to re-think their disaster recovery and business continuity strategies due to the recent spike in ransomware attacks in recent years, but also because of malware infection in general and how it operates. Many enterprise owners and staff don’t even know what a ransomware attack looks like. And, with its covert ability to sneak into IT networks virtually undetected, organizations and enterprises are having to make cybersecurity and disaster recovery a main priority, right alongside sales, productivity, and accounting.
For those of you still getting familiarized with it, ransomware is a type of malware that encrypts the files on a computer, then holds them hostage for a ransom fee in order to regain access. It normally spreads through email phishing attacks, exploit kits, removable drives or external network shares. New strains have appeared online with alarming frequency, and traditional antivirus programs cannot prevent these attacks until they have been identified – too late, in most cases, leaving many small and medium-sized businesses open to a data loss disaster.
Here, we aim to investigate and advise on the preparedness of decision-makers at small-to-midsize businesses (SMBs), so they may better protect their ventures against malware cyberattacks, and provide advice from IT security experts on how to avoid disaster. One of the most salient pieces of advice given by experts – and the FBI alike – is to never pay the ransom fee. Instead, consult with an IT services expert, who will generally be able to go in and bypass the malware program’s link to a C&C server, and thus halt the efficacy of the attack.
What Ransomware Looks Like
Because many business owners still have no basic working understanding of what ransomware even looks like or how it operates, here is some graphic evidence for your edification. Ransomware uses encryption to lock-up your database in a very aggressive way. It uses a public-private key encryption interface or procedure to do so. With great stealth, it uploads its file “payload” onto hard drives. One such example looks like this:
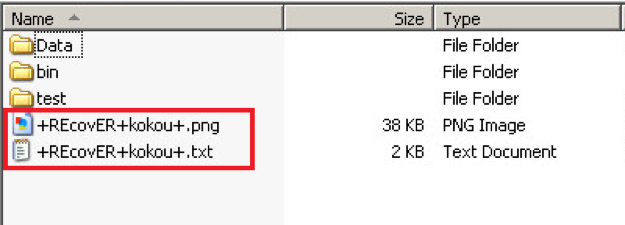
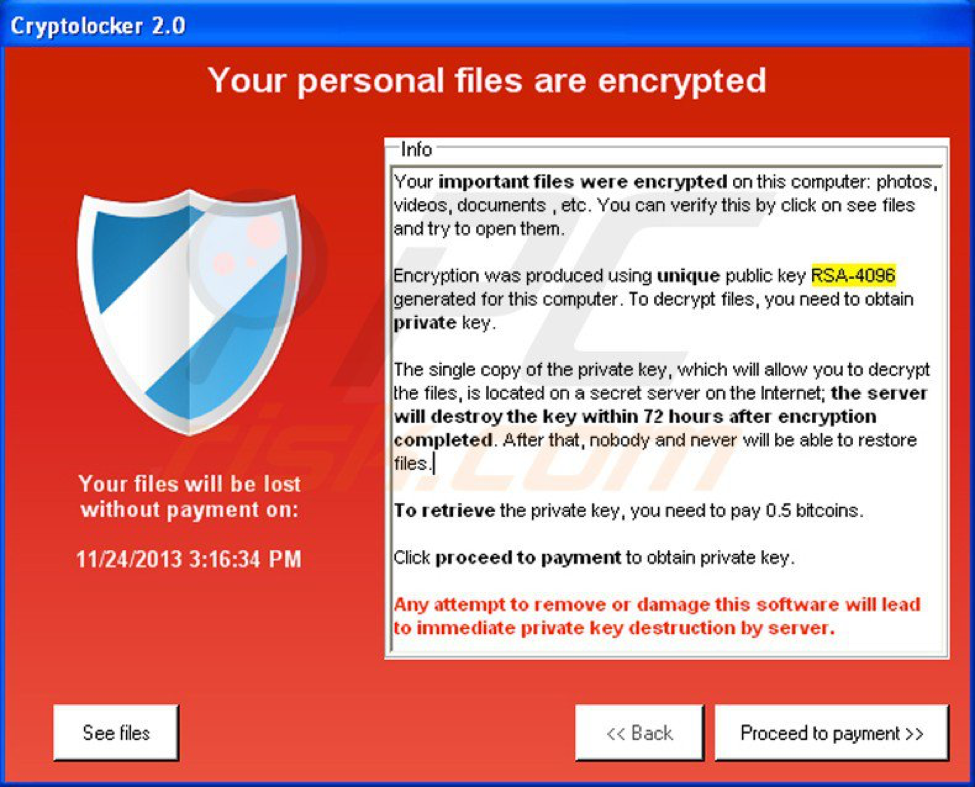
The ransomware files are in red, where the file-encrypting and “ransom note” files, respectively, sit in your system cache. Ransomware works so fast to encrypt and lock up your files now that total file encryption of your entire database can happen within a few minutes of you inadvertently clicking on a “mimic” email link. The ransom note will demand a certain amount of money – generally requested in Bitcoins – in order to obtain the private decryption key housed on a command and control (C&C) server which is running the operation remotely. Here’s a graphic of what a CryptoLocker attack looks like:
Facts on Malware Attacks and SMBs:
- 67% of SMB executives claim they would never pay a ransom to regain access to company files if their systems were infected with ransomware.
- Only 23% of SMBs in one sample say they are “very confident” their data is secure from a ransomware attack.
- A mere 31% of SMBs have irregular or non-existent file backup, meaning they would forfeit their files in an attack.
- Only 34% of SMBs test their file backups regularly to ensure that their data has been properly saved and is retrievable.
- Almost one-quarter, or 23% of SMBs say they currently do not have a disaster recovery plan for restoring backed-up data.
(Facts on Malware Source: SoftwareAdvice.com)
These are troubling statistics to be sure. Ideally, closer to 100% of respondents would say they would never pay a ransom fee to cybercriminals to unlock their files. Especially since new strains of ransomware will still kill your files anyway, even after you’ve paid. And, those low numbers on file backup and disaster recovery readiness need to be much higher as well, as just one day of downtime can cause great financial harm, let alone permanent data loss.
Get Expert Help for Ransomware Readiness
If you have questions regarding better disaster recovery planning and preventing ransomware attacks, eSOZO Computer and Network Services is a proven leader in providing IT consulting and cybersecurity in New Jersey. Contact one of our expert IT staff at (888) 376-9648 or send us an email at info@esozo.com today, and we can help you with all of your data defense and disaster recovery planning needs.
Author: Aaron White, Date: 5th October 2016




Follow eSOZO on Social Media